Most network administrators have at some point or another wished telnet worked for UDP as well as TCP.
Because of UDP being a connectionless transport protocol, scanning UDP ports is a bit more tricky than issuing the command “telnet smtp.mailserver.com 25”.
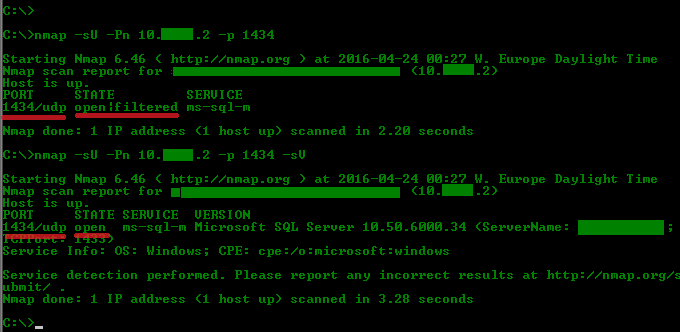
A normal UDP scan will typically yield “open|filtered” because the server does not respond to the UDP packet – or the packet was silently dropped in a firewall.
If there actually was a connection with the server, but no service was running at that particular port, you would get an ICMP Unreachable message and a scan would list the port as “closed”.
Now, using Nmap to verify whether or not UDP port 1434 is open through your firewall, simply issue the following command.
nmap -sU -Pn IP/FQDN -p 1434 -sV
This will work because the -sV switch instructs Nmap to probe potentially open ports for known services.
The switches explained
-sU – “UDP scan”
-Pn – “Treat all hosts as online — skip host discovery”
-sV – “Probe open ports to determine service/version info”
-p – “Only scan specified ports”
Have a look at the picture below to see the difference with and without the -sV switch.
Nmap should be in every network administrators tool chest and is available for a lot of platforms (Unix, Linux, Windows to mention a few).
There is also a portable version for Windows available.