In this guide we will setup an OpenGear ACM5004 for remote mgmt and remote SSH capabilities (serial ports) over the mobile network, utilizing DynDNS to enable easy connection to the device.
A fair warning first, I would not use the OpenGear over cellular networks as a permanent solution to access any equipment. The reason being that OpenGears own firewall and security settings is the only protection between the bad guys and the console port of your network equipment.
It can be configured to fail over to cellular networks in case remote access over LAN fails, which may be a more feasible solution.
Personally I use OpenGear remote on a case-by-case basis for when I need to be at two locations at once.
Contents
Default settings
By default, the device can be accessed through https://192.168.0.1 and using login credentials “root” / “default”
LAN settings
First off, head over to System > IP on the left hand side and configure the network parameters – typically DHCP.
User credentials
Head over to System > administration and change the password for root.
Next, go to Serial & Network > Users & Group and configure a new user.
In my example, I have created a user called “remotessh” with access to all ports, but without any group membership.
Cellular settings
Go to System > Dial > The tab Internal Cellular Modem. There you choose “Allow outgoing modem communication” before you enter the pin code, by clicking a button labeled “Unlock”.
Furthermore, you need to acquire an APN from your provider, which gives you a public IP rather than a private address on the cellular modem. In my case, using Telenor, the APN is internet.public. Your mobile services provider can supply your with the correct APN.
Dynamic DNS
Since the cellular modem will get a new IP address every time it connects to the GSM network, utilizing a dynamic DNS service is a must. Otherwise you would have to connect to LAN-port and retrieve the IP address manually every time you need to connect remote. (Sounds a bit counterproductive, don’t you think?)
The DynDNS settings used are as follows.
Verifying cellular connectivity
You can verify connectivity both from the dashboard and from Status > Statistics > The tab Failover & Out-of-band / Celluar as shown in the picture below.
And if you have connectivity, you should also DynDNS updated.
Setting up the serial ports
These settings are edited from the menu Serial & Network > Serial Port
Go into one of the ports (or all of them) and tick off “Console Server Mode” and make sure only SSH is ticked off
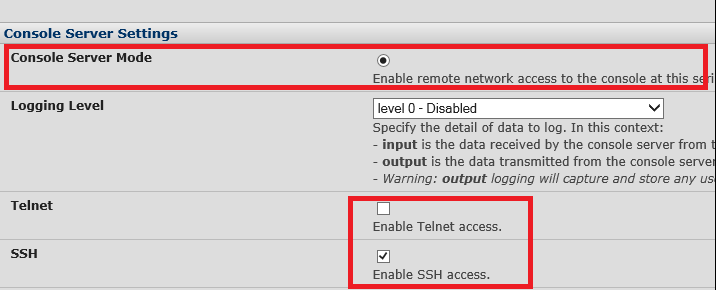
After you have edited all the ports, it should look something like this:

Setting up Security
Now, as mentioned in the warning, the only thing that stands between your equipments console port and the bad guys, are the OpenGear ConsoleServer – which is not created by and infosec company. Regardless, we should secure it as much as possible.
Service access
In System > Services > The Tab Service Access we can ensure that only HTTPS/SSH and SSH to serial ports are ticked off in the coloumn “Dialout/Cellular”
Brute force protection
From the same menu, in the tab Brute Force you can enable protection for Brute Force attacks against your OpenGear equipment.

Firewall rules
Since we have allowed remote management on the Dialout/Cellular Service access anyone can connect the Console Server. Tighting down this can be done in the built in firewall of the device.
You can access the firewall from System > Firewall > The tab Firewall rules.
As shown my example below, I have granted SSH/HTTPS access from my public IP address.
I have allowed access to port 3001-3004 (the serial ports) from anywhere.
And I have blocked everything else.
A small note, if you would like to connect to the serial port menu from anywhere, you would need to allow SSH from anywhere as well. (See “connecting to the serial ports” below)
Connecting to the serial ports
To connect to serial port 1 you would simply SSH yourself into the device on port 3001.
Serial port 2: Port 3002
Serial port 3: Port 3003
Serial port 4: Port 3004
putty -ssh opengear.dyndns.com 3001
If you would like to connect to the menu and choose the port from there, you would have to allow SSH access into the device as well.
You will also need to use the username “remotessh:serial” as shown in the picture below
By now you should be good to go for remote access to your equipment! Happy configuration! =)







Nice write up! Fair point about layering security, Opengear’s recommendation is to use VPN when your cellular OOB IP isn’t behind carrier NAT:
https://opengear.zendesk.com/hc/en-us/articles/216375603-Cellular-security-best-practices
https://opengear.zendesk.com/hc/en-us/articles/216375003-Should-I-use-VPN-to-secure-my-connection-
Also FYI you can drop back to the serial port menu (pmshell chooser) from any session including a direct connection to e.g. 3001 with this escape sequence:
~m
Disclaimer: I work for Opengear.